How to resolve 'no matching key exchange method found' issue when using git commands
1. Purpose
In this post, I will demonstrate how to resolve the following issue when using the git pull command:
Unable to negotiate with 10.1.1.2: no matching key exchange method found.Their offer: diffie-hellman-group1-sha1fatal: Could not read from remote repository.2. Environment
- Client OpenSSH version: OpenSSH_8.5
- Server OpenSSH version: OpenSSH_7
3. The Problem and Solution
3.1 The Problem
When executing git pull or git clone commands over SSH to a Git server, if the OpenSSH versions do not match, the problem may occur.
As shown in the image above, if you connect to the server with a higher version of OpenSSH, the following error may occur:
Unable to negotiate with 10.1.1.2: no matching key exchange method found.Their offer: diffie-hellman-group1-sha1fatal: Could not read from remote repository.3.2 Debugging
You can debug the issue using the following command:
$ GIT_SSH_COMMAND="ssh -vvv" git pullOpenSSH_8.5, OpenSSL 1.1.1k 12 Mar 2021debug1: Reading configuration data ...3.3 The Solution
The problem is caused by a mismatched key exchange algorithm in OpenSSH. The error message indicates that the server requires the diffie-hellman-group1-sha1 algorithm, but it is not supported locally. You can configure the local OpenSSH to support this algorithm.
Open your ~/.ssh/config file and configure it as follows (assuming your server’s IP address is 10.1.1.2):
Host 10.1.1.2 KexAlgorithms +diffie-hellman-group1-sha1Execute the git command again:
➜ bswen git:(master) ✗ git pullAlready up to date.➜ bswen git:(master) ✗Now it works!
3.4 Why Did This Happen?
When a Git client tries to connect to a Git server, it uses the SSH protocol. The problem is caused by an algorithm mismatch between the client and server.
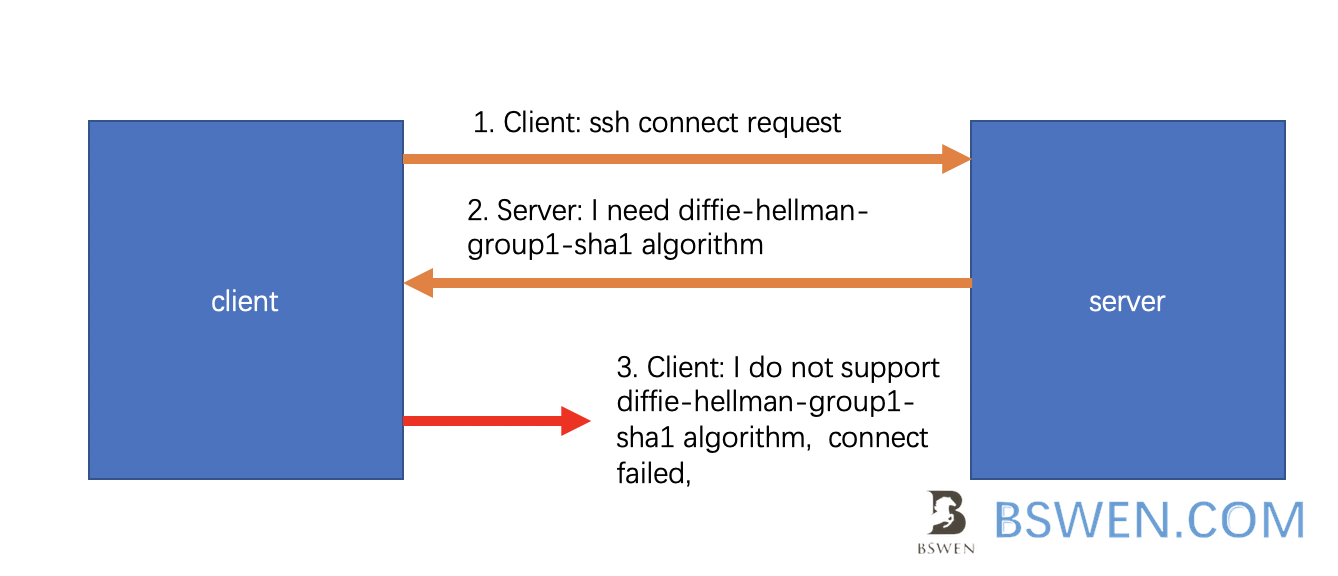
When an SSH client connects to a server, each side offers lists of connection parameters to the other. These parameters include:
KexAlgorithms: The key exchange methods used to generate per-connection keys.HostkeyAlgorithms: The public key algorithms accepted for an SSH server to authenticate itself to an SSH client.Ciphers: The ciphers used to encrypt the connection.MACs: The message authentication codes used to detect traffic modification.
For a successful connection, there must be at least one mutually-supported choice for each parameter.
If the client and server cannot agree on a mutual set of parameters, the connection will fail. OpenSSH (7.0 and greater) will produce an error message like this:
Unable to negotiate with legacyhost: no matching key exchange method found.Their offer: diffie-hellman-group1-sha1In this case, the client and server were unable to agree on the key exchange algorithm. The server offered only the diffie-hellman-group1-sha1 method. OpenSSH supports this method but does not enable it by default because it is considered weak and potentially vulnerable to the Logjam attack.
You can find more information about this change on this website.
4. Summary
In this post, I demonstrated how to resolve the no matching key exchange method found error when using the SSH protocol to connect to an SSH server. The key point is that both the client and server must have at least one common algorithm to establish a successful connection.
Final Words + More Resources
My intention with this article was to help others share my knowledge and experience. If you want to contact me, you can contact by email: Email me
Here are also the most important links from this article along with some further resources that will help you in this scope:
Oh, and if you found these resources useful, don’t forget to support me by starring the repo on GitHub!